MoTB #07: Reflected XSS vulns in yfrog
What is yfrog
"yfrog is a service run by ImageShack that lets you share your photos on and videos on Twitter." (yfrog FAQ page)
Twitter affect
yfrog can be used to send tweets by uploading new photos, or posting comments on existing photos.
yfrog is using OAuth authentication method in order to utilize the Twitter API.
Popularity rate
A competitor to TwitPic in the Twitter photo sharing market. Owned and operated by the popular ImageShack photo sharing service provider - 4 twits




Vulnerability: Reflected Cross-Site Scripting in the Upload and Search pages.
Status: Patched.
Details: The yfrog picture upload page does not encode HTML entities in the "url" variable, which can allow the injection of scripts. Similar vulnerability exists in the "s" variable of the yfrog Search page.
This vulnerability could have allowed an attacker to send tweets on behalf of its victims.
Proof-of-Concepts:
http://yfrog.com/?url=xxx">%3Cscript%3Ealert%28"xss"%29%3C%2Fscript%3E
http://yfrog.com/search.php?s=%3Cscript%3Ealert%28/xss/%29%3C%2Fscript%3E
Screenshots:
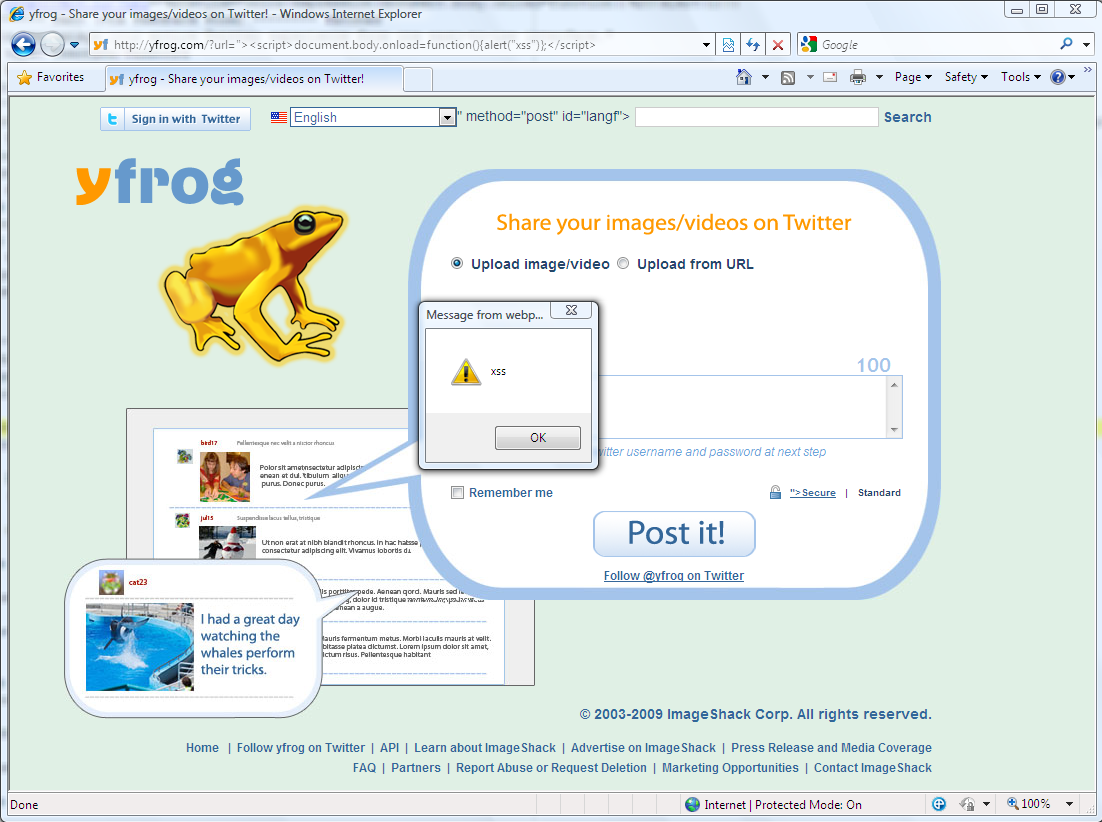
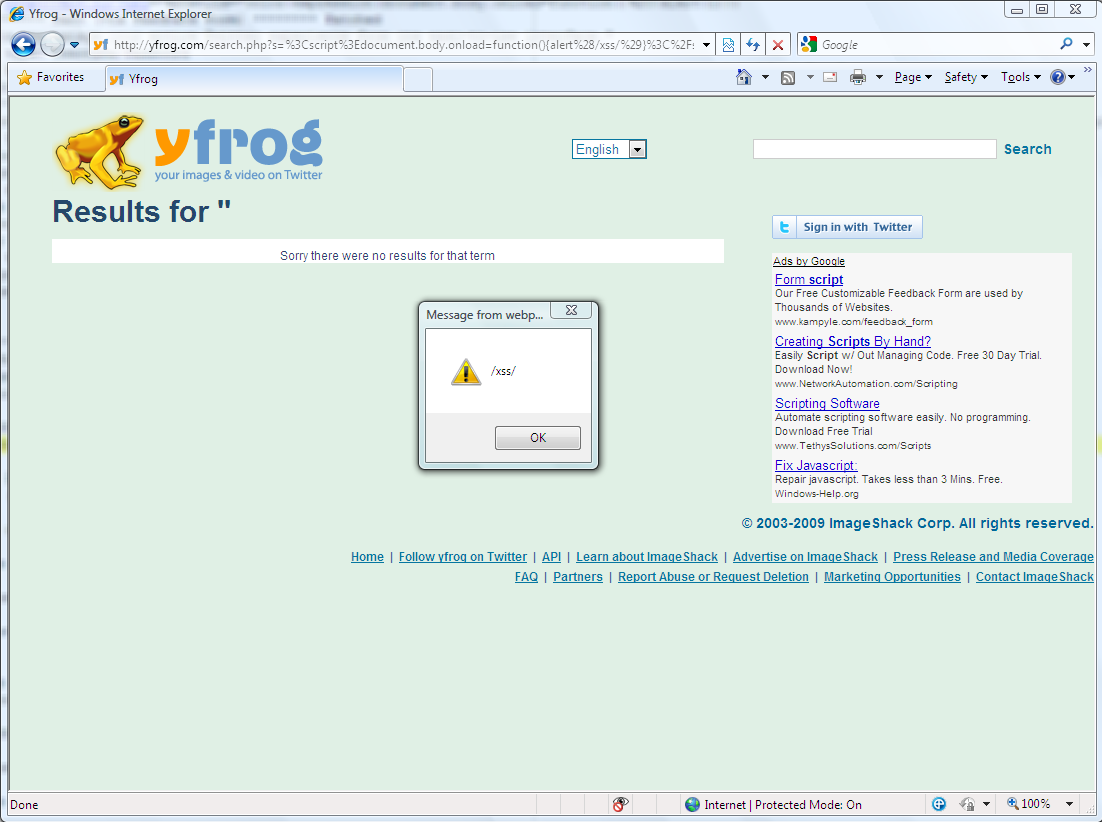
Vendor response rate
The vulnerabilities were fixed 3 hours after they were reported. Excellent - 5 twits.





"yfrog is a service run by ImageShack that lets you share your photos on and videos on Twitter." (yfrog FAQ page)
Twitter affect
yfrog can be used to send tweets by uploading new photos, or posting comments on existing photos.
yfrog is using OAuth authentication method in order to utilize the Twitter API.
Popularity rate
A competitor to TwitPic in the Twitter photo sharing market. Owned and operated by the popular ImageShack photo sharing service provider - 4 twits




Vulnerability: Reflected Cross-Site Scripting in the Upload and Search pages.
Status: Patched.
Details: The yfrog picture upload page does not encode HTML entities in the "url" variable, which can allow the injection of scripts. Similar vulnerability exists in the "s" variable of the yfrog Search page.
This vulnerability could have allowed an attacker to send tweets on behalf of its victims.
Proof-of-Concepts:
http://yfrog.com/?url=xxx">%3Cscript%3Ealert%28"xss"%29%3C%2Fscript%3E
http://yfrog.com/search.php?s=%3Cscript%3Ealert%28/xss/%29%3C%2Fscript%3E
Screenshots:


Vendor response rate
The vulnerabilities were fixed 3 hours after they were reported. Excellent - 5 twits.





