MoTB #04: CSRF in BigTweet
What is BigTweet
"BigTweet was developed by Scott Carter (@scott_carter) as a way to interact more effectively with various networks from the Web. When you click on the BigTweet bookmarklet, a window appears in the middle of your current web page. Use it to post to Twitter or FriendFeed and then return to what you were doing. It doesn't get any faster." (BigTweet home page)
Twitter affect
BigTweet can be used to send tweets from any web page by using a bookmarklet.
BigTweet is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
While Bigtweet is not on any of the top Twitter services lists, it has an easy to integrate bookmarklet interface - 1 twit

Vulnerability: Cross-Site Request Forgery in BigTweet upate.json.
Status: Patched.
Details: The bigtweet update.json web page did not use authenticity code in order to validate that the HTTP post is coming from the bigtweet web application.
Screenshots:
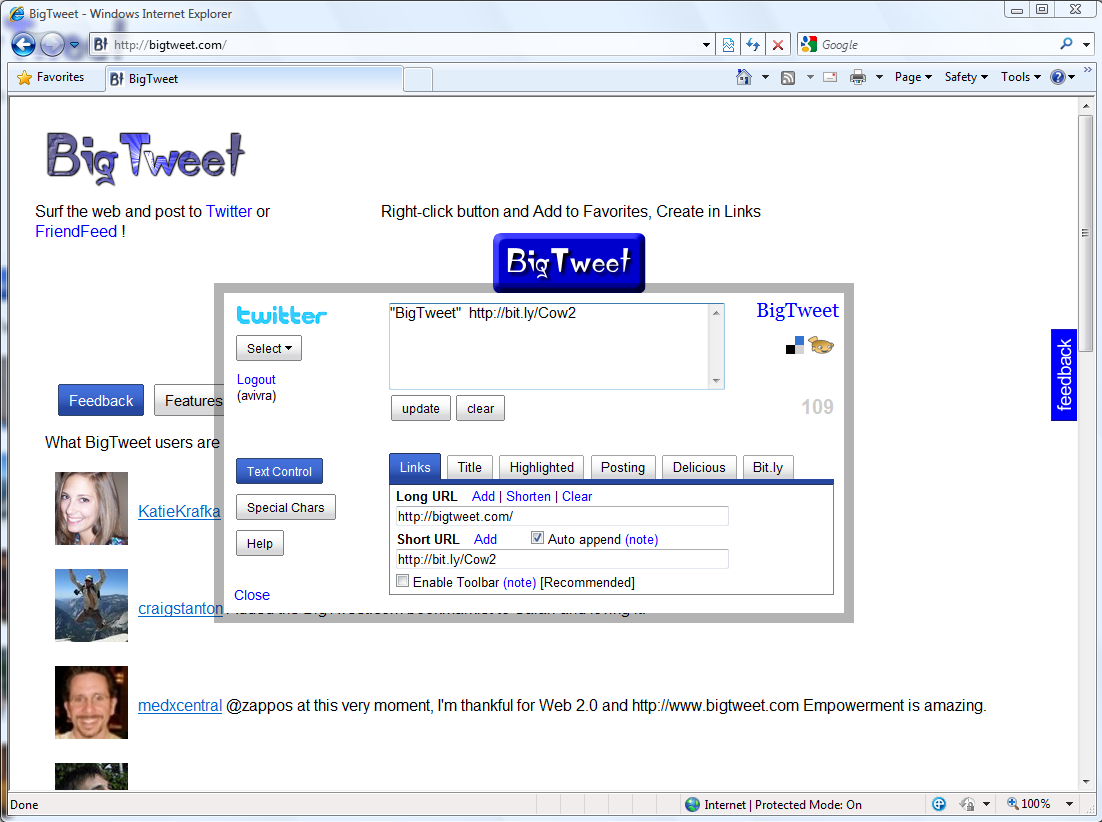
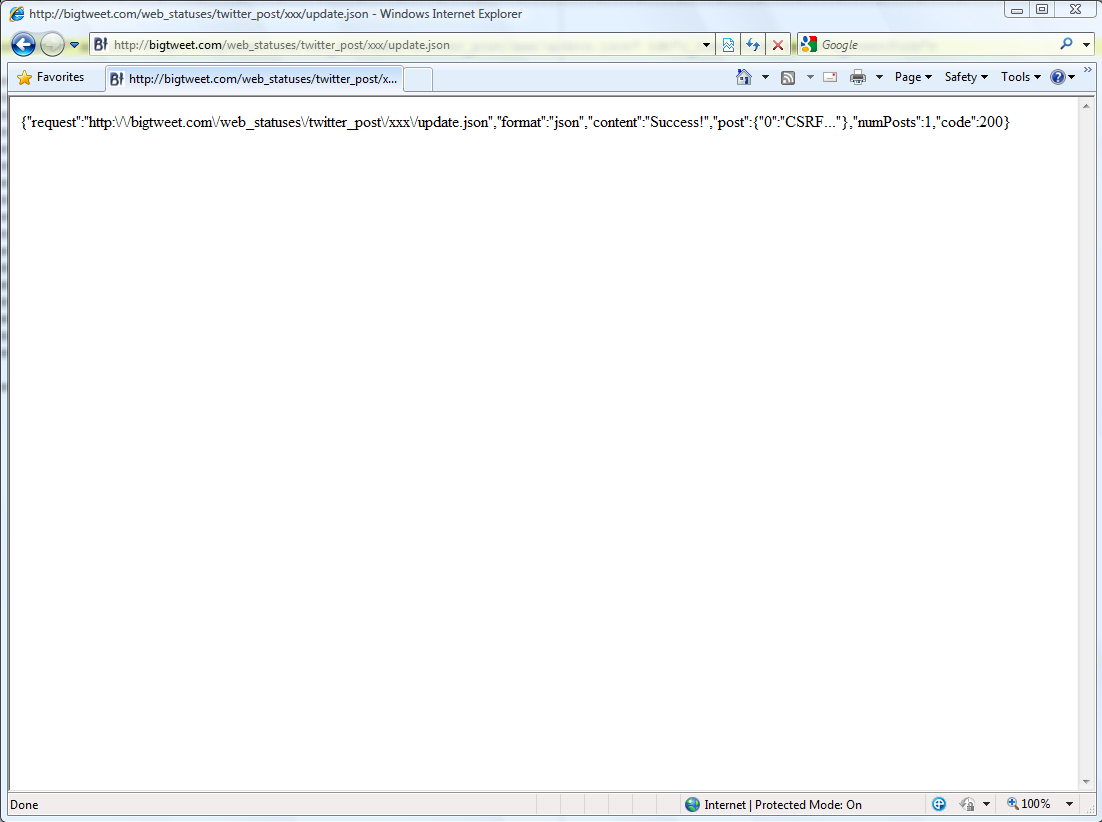
Note: While the proof-of-concept in the screenshots used the "xxx" twitter user, the page will actually send a tweet for the currently logged-in user (in the PoC - @avivra). Any bigtweet.com registered user could have been used instead of xxx.
Vendor response rate
Vulnerability was fully fixed 22 hours after it has been reported.
Scott Carter, the developer of BigTweet, is also the one who came up with the idea of having a security best practices document for API developers. Alex Payne from Twitter has written such document last week. Excellent - 5 twits.





"BigTweet was developed by Scott Carter (@scott_carter) as a way to interact more effectively with various networks from the Web. When you click on the BigTweet bookmarklet, a window appears in the middle of your current web page. Use it to post to Twitter or FriendFeed and then return to what you were doing. It doesn't get any faster." (BigTweet home page)
Twitter affect
BigTweet can be used to send tweets from any web page by using a bookmarklet.
BigTweet is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
While Bigtweet is not on any of the top Twitter services lists, it has an easy to integrate bookmarklet interface - 1 twit

Vulnerability: Cross-Site Request Forgery in BigTweet upate.json.
Status: Patched.
Details: The bigtweet update.json web page did not use authenticity code in order to validate that the HTTP post is coming from the bigtweet web application.
Screenshots:


Note: While the proof-of-concept in the screenshots used the "xxx" twitter user, the page will actually send a tweet for the currently logged-in user (in the PoC - @avivra). Any bigtweet.com registered user could have been used instead of xxx.
Vendor response rate
Vulnerability was fully fixed 22 hours after it has been reported.
Scott Carter, the developer of BigTweet, is also the one who came up with the idea of having a security best practices document for API developers. Alex Payne from Twitter has written such document last week. Excellent - 5 twits.





