MoTB #20: Insecure communication vulnerability in twhirl
What is twhirl
"twhirl is a desktop client for the Twitter microblogging service. Most of the features available on the Twitter website are accessible through twhirl, too." (twhirl about page)
Twitter effect
twhirl can be used to send tweets, direct messages and follow/unfollow other Twitter users from multiple Twitter accounts.
twhirl is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
One of the most popular Twitter clients. 7th place in the most used twitter clients - 4.5 twits





Vulnerability: Insecure communication vulnerability in the update proccess.
Status: Unpatched.
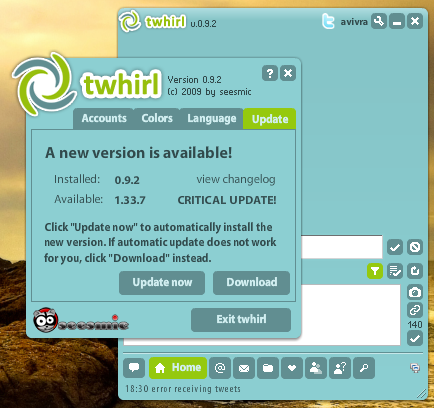
Details: twhirl does not use a secure communication when it checks for updates. An attacker who controls the victim's network (e.g. via public WiFi, compromised DNS servers, etc.) can tamper with the request to http://www.twhirl.org/version.xml, and replace the values of both "version" and "installerURL" XML entities, in order to force a display of fake (malicious) update.
This vulnerability can be used by an attacker to install malware on its victims machines.
Screenshot:
Vendor response rate
The vendor (Seesmic) have decided not to confirm this as a vulnerability. Seesmic claims that they "do not believe this exploit is possible due to the way Adobe AIR binaries are signed at compilation time with private keys to create both an ApplicationID and a PublisherID". While this might be true, an attacker can:
1) Direct the user to automatically install old signed version of twhirl, and then exploit other vulnerabilities that were patched by newer versions.
2) Use an unsigned binary, which might cause the automatic download to fail. In this case, the user will follow twhirl's request (See above screenshot) and manually download and run the malicious executable.
Instead of applying a one character fix to this vulnerability (by simply adding an "s" to the HTTP request), Seesmic have decided to ignore my continuous requests to fix this vulnerability. Very poor - 0.5 twits.

"twhirl is a desktop client for the Twitter microblogging service. Most of the features available on the Twitter website are accessible through twhirl, too." (twhirl about page)
Twitter effect
twhirl can be used to send tweets, direct messages and follow/unfollow other Twitter users from multiple Twitter accounts.
twhirl is using Username/Password authentication in order to utilize the Twitter API.
Popularity rate
One of the most popular Twitter clients. 7th place in the most used twitter clients - 4.5 twits





Vulnerability: Insecure communication vulnerability in the update proccess.
Status: Unpatched.
Details: twhirl does not use a secure communication when it checks for updates. An attacker who controls the victim's network (e.g. via public WiFi, compromised DNS servers, etc.) can tamper with the request to http://www.twhirl.org/version.xml, and replace the values of both "version" and "installerURL" XML entities, in order to force a display of fake (malicious) update.
This vulnerability can be used by an attacker to install malware on its victims machines.
Screenshot:

Vendor response rate
The vendor (Seesmic) have decided not to confirm this as a vulnerability. Seesmic claims that they "do not believe this exploit is possible due to the way Adobe AIR binaries are signed at compilation time with private keys to create both an ApplicationID and a PublisherID". While this might be true, an attacker can:
1) Direct the user to automatically install old signed version of twhirl, and then exploit other vulnerabilities that were patched by newer versions.
2) Use an unsigned binary, which might cause the automatic download to fail. In this case, the user will follow twhirl's request (See above screenshot) and manually download and run the malicious executable.
Instead of applying a one character fix to this vulnerability (by simply adding an "s" to the HTTP request), Seesmic have decided to ignore my continuous requests to fix this vulnerability. Very poor - 0.5 twits.


1 Comments:
what about xss/iframe and redirect? check "Password Reset" module
http://img16.imageshack.us/img16/3900/23859750.png
and
http://img16.imageshack.us/img16/870/20891524.png
Post a Comment
<< Home